Manage Distributed Secrets in Applications on Cloud Foundry With Spring Cloud Vault
Andreas Falk
12 October 2017
Sources and Presentation: https://github.com/andifalk/cf-summit-2017
Andreas Falk
NovaTec Consulting GmbH (Stuttgart/Germany)
Authentication (OAuth2/OIDC): OK!
Authorization: OK!

What about sensitive data?
A6: Sensitive Data Exposure

EU General Data Protection Regulation (GDPR)
Privacy by Design
Breach Notification
Typical Sensitive Data
Passwords
Service credentials (DB, Messaging, ...)
OAuth2 client secrets
Encryption keys
Credit card numbers
Social security numbers
Application-xxx.Yaml
Database access credentials
spring:
datasource:
url: jdbc:postgresql://localhost/test
username: root
password: mysupersecretpassword
Key Management

Agenda: Security Evolution

Introduction
 https://www.vaultproject.io
https://www.vaultproject.io
Vault
A Tool for Managing Secrets like...
- Tokens
- Passwords
- X.509 Certificates
- API keys
- DB credentials
- And other secrets...
Vault
“A Security Swiss Army Knife”
Jeff Mitchell, Vault Lead at HashiCorp
Key Features
Secure Secret Storage
Dynamic Secrets
Data Encryption (AES cypher)
Leasing, Renewal & Revocation
Operational Features
Authentication
Authorization (ACL)
Audit Logs
High Availability Mode (HA)
Architecture
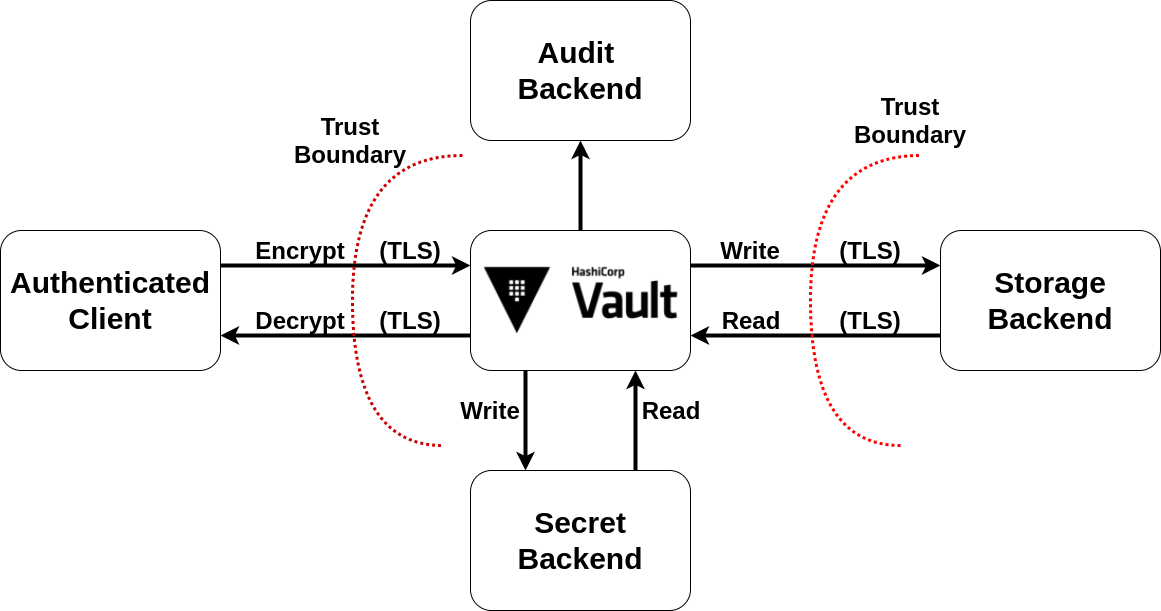
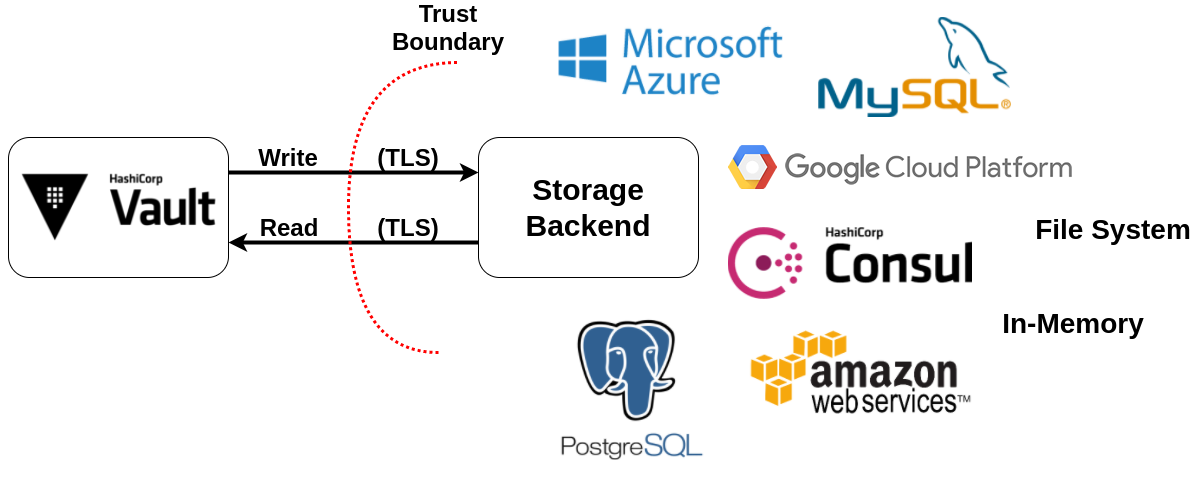
Vault Storage
Vault Secrets

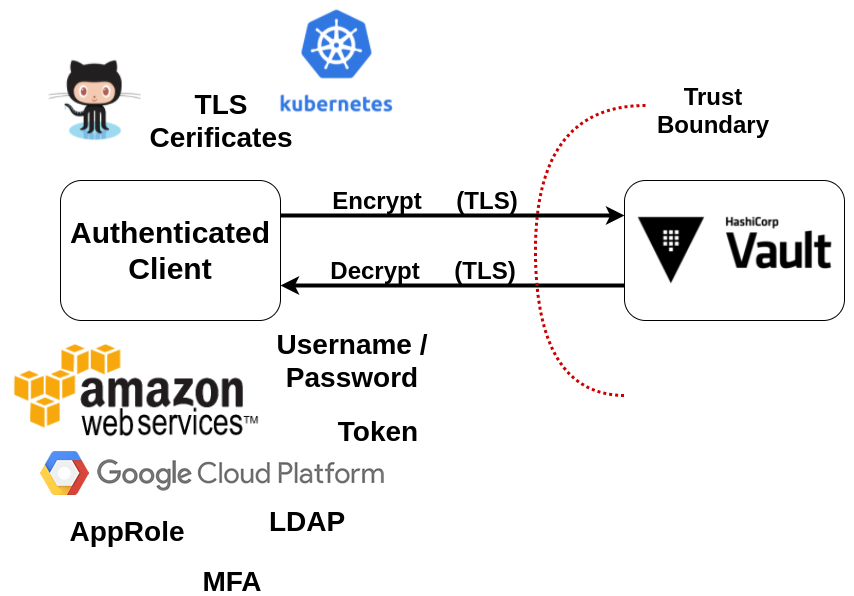
Vault Authentication
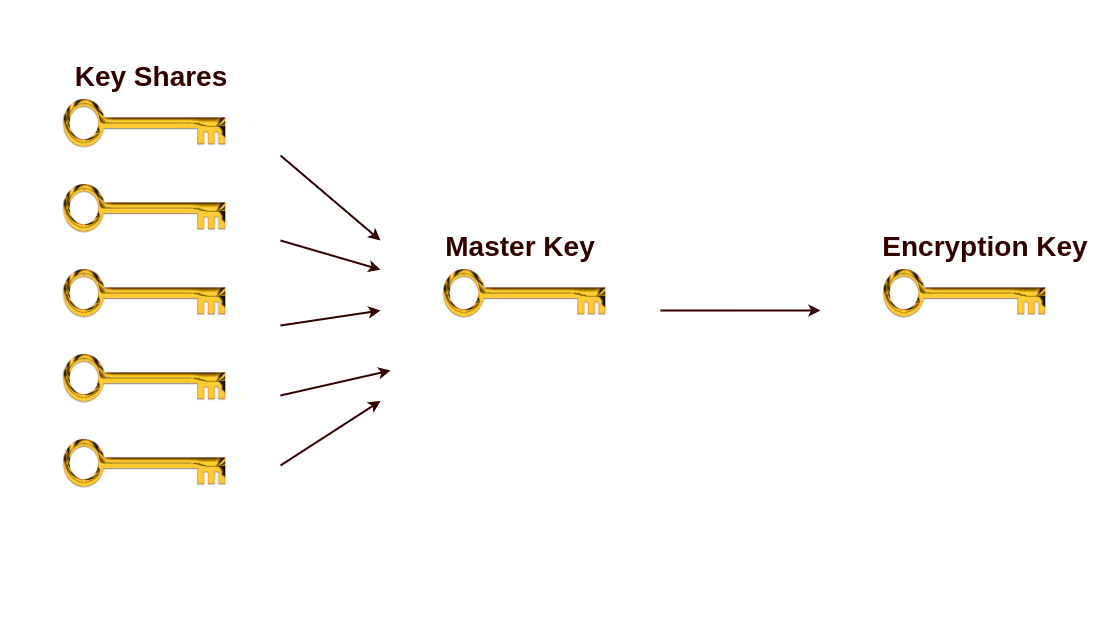
Vault Key Shares
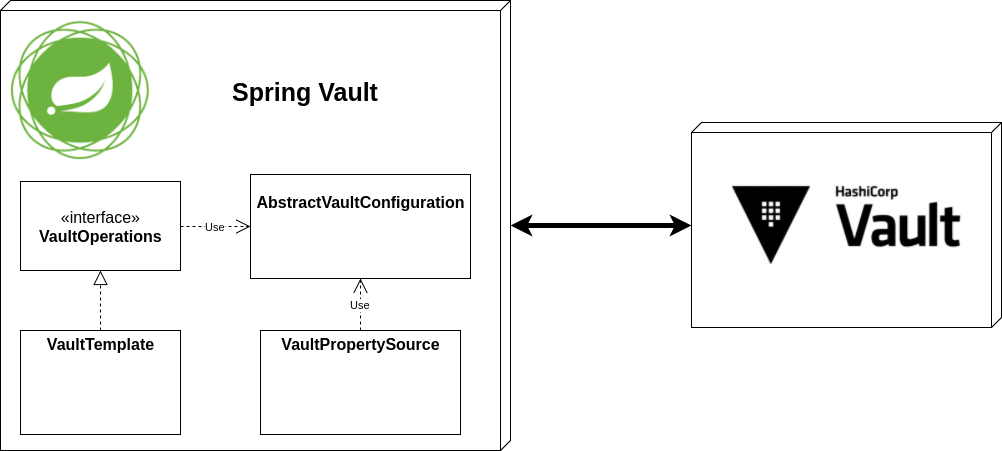
Spring Vault

Encryption as a service

Spring Cloud Vault


Secret vault mapping
bootstrap.properties
spring.cloud.vault.generic.application-name =
application1,additional/keys
#spring.cloud.vault.application-name = ...
#spring.application.name = ...
Mapped secret paths in vault
/secret/application1
/secret/application1/myprofile
/secret/additional/keys
/secret/application
/secret/application/myprofile
Rotate Database Credentials
bootstrap.yml
spring.cloud.vault:
postgresql:
enabled: true
role: readonly
backend: postgresql
username-property: spring.datasource.username
password-property: spring.datasource.username

Spring Cloud Config Vault Environment Repository
application.properties (Config Server)
spring.profiles.active=git,vault
spring.cloud.config.server.vault.host=127.0.0.1
spring.cloud.config.server.vault.port=8200
spring.cloud.config.server.vault.scheme=https
bootstrap.properties (Client)
spring.cloud.config.token = YourVaultToken
 https://github.com/hashicorp/vault-service-broker
https://github.com/pivotal-cf/spring-cloud-vault-connector
https://github.com/hashicorp/vault-service-broker
https://github.com/pivotal-cf/spring-cloud-vault-connector
Q&A
http://www.novatec-gmbh.de http://blog.novatec-gmbh.de
andreas.falk@novatec-gmbh.de
@NT_AQE, @andifalk
References
- Spring Cloud Config (https://cloud.spring.io/spring-cloud-config/)
- Shamir's secret sharing (https://en.wikipedia.org/wiki/Shamir's_Secret_Sharing)
- Spring Cloud Vault (https://cloud.spring.io/spring-cloud-vault)
- Vault (https://www.vaultproject.io)
- Cloud Foundry Vault Service Broker (https://github.com/hashicorp/vault-service-broker)
- Sources and Presentation (https://github.com/andifalk/cfsummit2017)
All images used are from Pixabay and are published under Creative Commons CC0 license.
All used logos are trademarks of corresponding companies